Recovering the BIOS password from a Panasonic CF-U1 mk2 (AMI Aptio UEFI)
This was originally posted as a gist here: https://gist.github.com/en4rab/550880c099b5194fbbf3039e3c8ab6fd
A mess of my own making
While messing with a CF-U1 handheld PC that I bought off ebay I managed to mess up the BIOS and it seems it reverted to previous settings which included an unknown BIOS password, it would however still boot into windows. Since I could still boot windows I was able to dump the bios flash using AFUWINGUI.EXE the version I used was 3.09.03.1462 which is available here:
https://www.ami.com/support-other/ Click on Aptio 4 AMI Firmware Update Utility
There may be a more appropriate version to use as this seemed to have trouble checking the bios version when flashing but did work if you selected “Do Not Check ROM ID” but flashing isnt needed to get the password.
Dumping the flash
Run AFUWINGUI.EXE and at the bottom of the “Information” tab click the save button to make a backup of your bios, the default name is afuwin.rom Now open this saved image with UEFITool_NE available here:
https://github.com/LongSoft/UEFITool/releases
I used UEFITool_NE_A51_win32.zip later versions should work fine. The new engine (NE) verson seems to deal with AMI’s odd nvram format better.
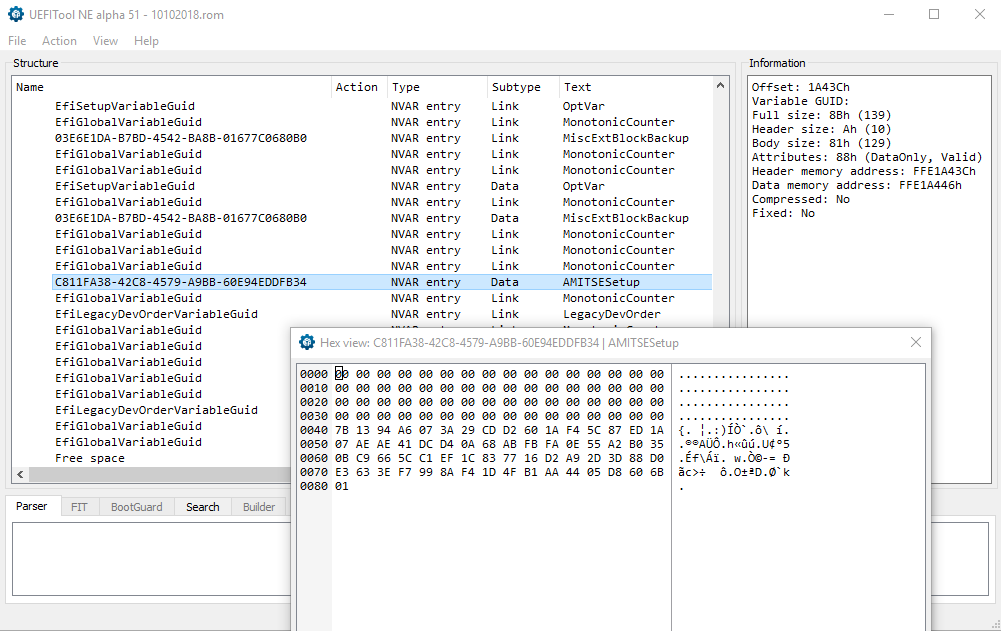
Expand the first EfiFirmwareFilesystemGuid » NVRAM dropdown tree and look for the GUID
C811FA38-42C8-4579-A9BB-60E94EDDFB34 (AMITSESetup)
with subtype Data there will be others with subtype Link which are older no longer valid entrys because of the odd way AMI nvram works, if you find one of these right click on it and select “Go to data” and it will take you to the actual data entry.
Now right click and select “Body hex view” and you should see something like:
1
2
3
4
5
6
7
8
9
0000 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0010 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0020 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0030 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0040 7B 13 94 A6 07 3A 29 CD D2 60 1A F4 5C 87 ED 1A {.”¦.:)ÍÒ`.ô\‡í.
0050 07 AE AE 41 DC D4 0A 68 AB FB FA 0E 55 A2 B0 35 .®®AÜÔ.h«ûú.U¢°5
0060 0B C9 66 5C C1 EF 1C 83 77 16 D2 A9 2D 3D 88 D0 .Éf\Áï.ƒw.Ò©-=ˆÐ
0070 E3 63 3E F7 99 8A F4 1D 4F B1 AA 44 05 D8 60 6B ãc>÷™Šô.O±ªD.Ø`k
0080 01
In this the bytes from 0x00 to 0x3F are the currently unset user password, 0x40 to 0x7F are the obfuscated administrator password and 0x80 is the quiet boot flag.
1337 encryption
The password is obfuscated using super secure xor
VOID PasswordEncode( CHAR16 *Password, UINTN MaxSize)
{
UINTN ii;
unsigned int key = 0x935b;
#if SETUP_PASSWORD_NON_CASE_SENSITIVE
for ( ii = 0; ii < MaxSize; ii++ )
Password[ii] = ((Password[ii]>=L'a')&&(Password[ii]<=L'z'))?(Password[ii]+L'A'-L'a'):Password[ii];
#endif
// Encode the password..
for ( ii = 1; ii <= MaxSize/2; ii++ )
Password[ii-1] = (CHAR16)(Password[ii-1] ^ (key*ii));
}
So Xoring the above encoded password:
1
2
7B 13 94 A6 07 3A 29 CD D2 60 1A F4 5C 87 ED 1A 07 AE AE 41 DC D4 0A 68 AB FB FA 0E 55 A2 B0 35
0B C9 66 5C C1 EF 1C 83 77 16 D2 A9 2D 3D 88 D0 E3 63 3E F7 99 8A F4 1D 4F B1 AA 44 05 D8 60 6B
with
1
2
5B 93 B6 26 11 BA 6C 4D C7 E0 22 74 7D 07 D8 9A 33 2E 8E C1 E9 54 44 E8 9F 7B FA 0E 55 A2 B0 35
0B C9 66 5C C1 EF 1C 83 77 16 D2 A9 2D 3D 88 D0 E3 63 3E F7 99 8A F4 1D 4F B1 AA 44 05 D8 60 6B
gives
1
2
20 80 22 80 16 80 45 80 15 80 38 80 21 80 35 80 34 80 20 80 35 80 4e 80 34 80 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Each character of the password is stored as 2 bytes, and as x86 is wrong endian im guessing should be read as 0x8020 0x8022 I have no idea where the 0x80 comes from possibly its something to do with the EFI_SHIFT_STATE_VALID in this case the password was lower case, possibly uppercase status is encoded in this byte too I have no idea I havent tested uppercase passwords.
WTF scancodes how does this map to keys
From the unobfuscated data you can see the password is 13 characters long, im going to ignore the 0x80 bytes as i dont understand them :P and just look at the others:
20 22 16 45 15 38 21 35 34 20 35 4e 34
They appear to be some sort of scancodes, although while googleing this I found some AMI bioses seem to use ascii here so you can read it out directly as text, but not on this machine.
When this CF-U1 arrived from ebay it had a password which i sucessfully guessed as “toughbook” my second guess would have been “panasonic” since using text written on the front of the PC as a password saves writing it under the battery cover :P
Looking through the older link entrys for the AMITSESetup nvram I found what I thought was the data for this password which deobfuscating as above gave (ignoring the 0x80):
1
2
35 39 37 24 25 14 39 39 27
t o u g h b o o k
This seemed promising repeated characters have the same value and gives a bit of a key to the mapping Some googeling later about UEFI scancodes and i found this page:
https://web.archive.org/web/20170627134759/http://wiki.phoenix.com/wiki/index.php/EFI_KEY
From this it seems the value is the offset into this enum so in the toughbook example 35 translates to EfiKeyD5 a second page I found gave the mapping from EfiKey to ascii:
https://github.com/tianocore/edk2/blob/master/MdeModulePkg/Bus/Usb/UsbKbDxe/KeyBoard.c#L36
So i made up a list of byte to ascii using these, below are just 0x10 to 0x4E to cover most values but not be too stupidly long.
| Hex | Char | EFIkey | Hex | Char | EFIkey |
|---|---|---|---|---|---|
| 10 | z | EfiKeyB1 | 30 | Tab | EfiKeyTab |
| 11 | x | EfiKeyB2 | 31 | q | EfiKeyD1 |
| 12 | c | EfiKeyB3 | 32 | w | EfiKeyD2 |
| 13 | v | EfiKeyB4 | 33 | e | EfiKeyD3 |
| 14 | b | EfiKeyB5 | 34 | r | EfiKeyD4 |
| 15 | n | EfiKeyB6 | 35 | t | EfiKeyD5 |
| 16 | m | EfiKeyB7 | 36 | y | EfiKeyD6 |
| 17 | , | EfiKeyB8 | 37 | u | EfiKeyD7 |
| 18 | . | EfiKeyB9 | 38 | i | EfiKeyD8 |
| 19 | / | EfiKeyB10 | 39 | o | EfiKeyD9 |
| 1A | EfiKeyRShift | 3A | p | EfiKeyD10 | |
| 1B | EfiKeyUpArrow | 3B | [ | EfiKeyD11 | |
| 1C | 1 | EfiKeyOne | 3C | ] | EfiKeyD12 |
| 1D | 2 | EfiKeyTwo | 3D | \ | EfiKeyD13 |
| 1E | 3 | EfiKeyThree | 3E | EfiKeyDel | |
| 1F | EfiKeyCapsLock | 3F | EfiKeyEnd | ||
| 20 | a | EfiKeyC1 | 40 | EfiKeyPgDn | |
| 21 | s | EfiKeyC2 | 41 | 7 | EfiKeySeven |
| 22 | d | EfiKeyC3 | 42 | 8 | EfiKeyEight |
| 23 | f | EfiKeyC4 | 43 | 9 | EfiKeyNine |
| 24 | g | EfiKeyC5 | 44 | ` | EfiKeyE0 |
| 25 | h | EfiKeyC6 | 45 | 1 | EfiKeyE1 |
| 26 | j | EfiKeyC7 | 46 | 2 | EfiKeyE2 |
| 27 | k | EfiKeyC8 | 47 | 3 | EfiKeyE3 |
| 28 | l | EfiKeyC9 | 48 | 4 | EfiKeyE4 |
| 29 | ; | EfiKeyC10 | 49 | 5 | EfiKeyE5 |
| 2A | ' | EfiKeyC11 | 4A | 6 | EfiKeyE6 |
| 2B | | | EfiKeyC12 | 4B | 7 | EfiKeyE7 |
| 2C | 4 | EfiKeyFour | 4C | 8 | EfiKeyE8 |
| 2D | 5 | EfiKeyFive | 4D | 9 | EfiKeyE9 |
| 2E | 6 | EfiKeySix | 4E | 0 | EfiKeyE10 |
| 2F | + | EfiKeyPlus |
So what was the password?
Using the above list and the recovered scancodes gave:
1
2
20 22 16 45 15 38 21 35 34 20 35 4e 34
a d m 1 n i s t r a t 0 r
and when i tried adm1nistrat0r it worked!
This is not complete as there are still questions about the 0x80 bytes but my guess is they encode the shift alt etc modifier keys but im back into my handheld so i’m not sure ill look further into it. This may also apply to other Aptio bioses as well as the Panasonic CF-U1, and if the machine isnt bootable you may be able to use a cheap spi adapter to dump the bios, in the case of the CF-U1 it uses an LPC flash which I don’t think you can get cheap clips and readers for and its buried in the machine so a nuisance to get to.
I just want to remove the password
Another option instread of trying to decode the password or if the password is stored as a sha1/sha256 hash is to dump the bios chip using an spi programmer. Open the spi dump and find the AMITSESetup data and just edit it with a hex editor to replace the obfuscated password with 00’s. This could then be flashed back using the spi flasher. Be aware on more modern AMI uefi’s there may be two copys of the NVRAM and the AMITSESetup needs to be edited in both copys.